Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam.
When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]
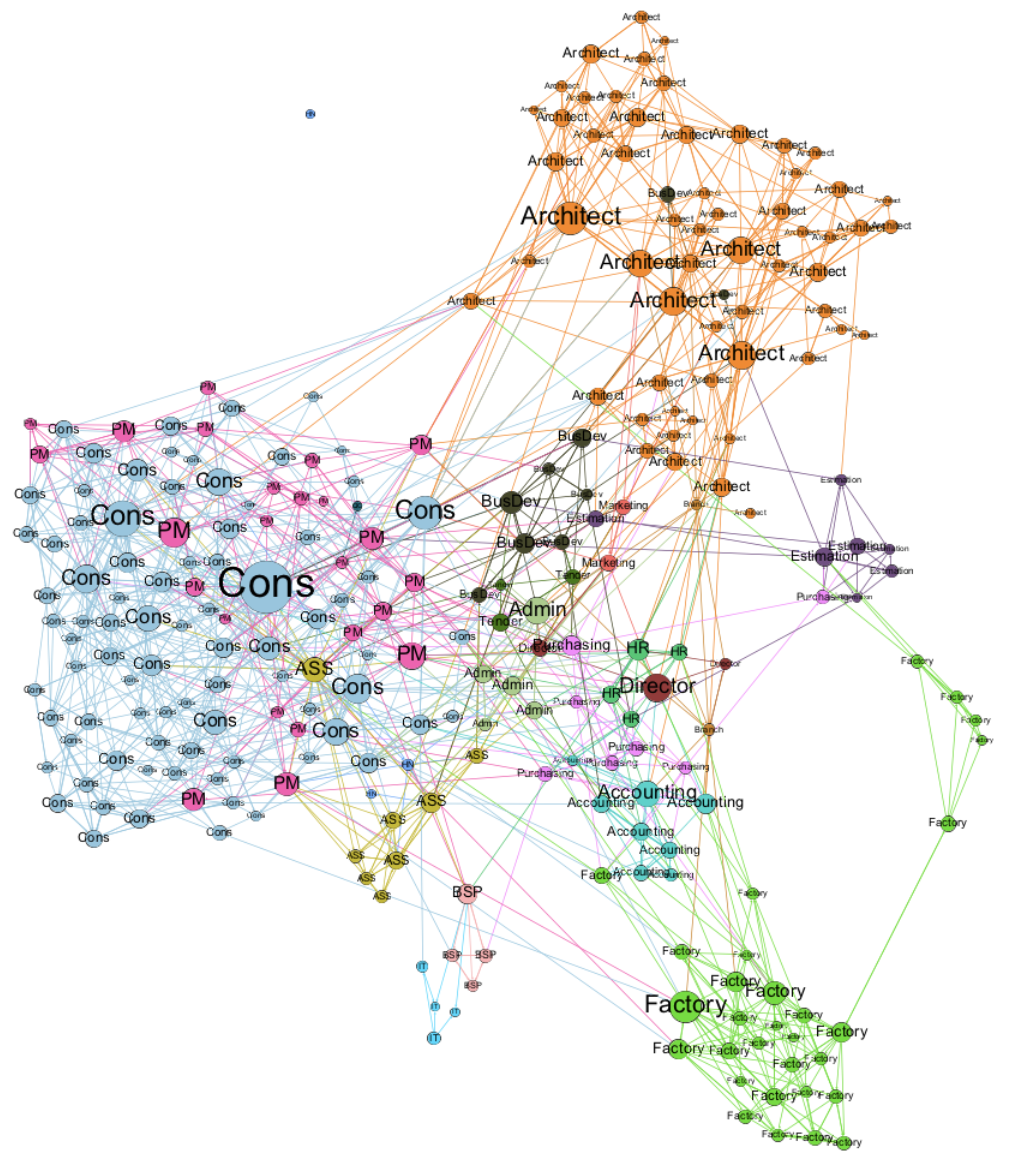
When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

When organizations think about cybersecurity, the conversation almost always starts with technology: firewalls, encryption, multifactor authentication. These tools are essential, but they often overshadow the fact that the weakest link in security is still people. Human employees make daily decisions about clicking links, sharing passwords, reporting incidents, or helping a colleague troubleshoot. Whether those choices […]

